
December 15, 2025
Managed IT Services for Alberta Private Career CollegesDiscover managed IT services for Alberta private career colleges. Boost security, compliance, and student success with a dedicated IT partnership.
Read Full Post%20(1).webp)
Usman Malik
Chief Executive Officer
November 6, 2025

Data security management is the comprehensive process of protecting your digital information from unauthorized access, modification, or theft—from its creation to its eventual deletion. It combines policies, procedures, and the right technology to ensure your organization's most valuable asset—its data—remains confidential, accurate, and available.
For Canadian businesses, this isn't just a recommendation from the IT department. It's a core operational necessity.
In the past, data security was often seen as a technical problem for the IT department to solve with software. That view isn't just outdated; it's dangerous. For modern Canadian small and medium-sized businesses (SMBs), effective data security management is a pillar of business survival. It directly impacts everything from your bottom line to your brand's reputation.
The fallout from a data breach extends far beyond getting your systems back online. Consider a real-world scenario: a mid-sized logistics company in Ontario. A single employee clicked on a convincing phishing email, and just like that, cybercriminals were inside their network.
The subsequent ransomware attack didn't just lock their files—it paralyzed their entire operation. Shipments were stranded, client data was exposed, and the company faced crippling downtime. The final bill? Hundreds of thousands of dollars in lost revenue and recovery costs.

This is why a proactive security program isn’t a "nice-to-have." The costs associated with a breach are complex and can be devastating for an SMB. To get data security right, you need to understand and implement robust security measures from the ground up.
These costs often stack up quickly and include:
Data security is no longer just about preventing hacks. It's about ensuring business continuity, protecting customer loyalty, and maintaining a competitive edge in a market where trust is everything.
Ultimately, proactive data security management is a direct investment in your company's future. It protects your operations, keeps you compliant, and—most importantly—preserves the customer trust that fuels your growth. Think of it as the foundational playbook for building a resilient, modern business.
Effective data security doesn’t begin with buying new software. It begins with understanding what you’re trying to protect. Before you can build your defences, you need a clear, honest picture of your data landscape and where your biggest vulnerabilities lie. This is what a risk assessment is all about—it's the crucial first step that demystifies your data and helps you focus your time and money where they’ll make a real difference.
A common mistake is turning this into a massive, complicated project. You don't need a team of analysts to get started. What you need is a practical, business-first approach. The goal is simple: identify your most critical data, understand the threats it faces, and prioritize your efforts accordingly.
The first step is to take an inventory of all the data your organization holds. Think of it like a stocktake for your information. You can't protect what you don't know you have. Since not all data is created equal, a straightforward classification system is essential to focus your security efforts effectively.
You can break your information down into a few simple categories:
Once you’ve sorted your data into these categories, the next step is to map out where it all lives. Is it on a local server in your office? Stored in a cloud application like Microsoft 365? Residing on employee laptops, or managed by a third-party payroll provider? Knowing its location is fundamental to securing it.
A risk assessment isn't just an IT exercise; it's a business strategy. It forces you to ask critical questions: What data, if lost or stolen, would cripple our operations or destroy our customers' trust? Answering that question is the foundation of a resilient security program.
With a clear inventory in hand, you can start to identify potential threats. A vulnerability is any weakness that a threat could exploit to compromise your data. This could be a technical gap, like unpatched software, or a human one, like an employee not trained to spot a phishing email.
Consider the common access points. Who can see your confidential client files? Is access truly limited to the accounting team, or can almost anyone on the network open that folder? Limiting access based on job roles—a concept known as the principle of least privilege—is one of the most effective ways to reduce your risk.
This analysis helps you connect specific threats to your most valuable data. For example, the risk of a ransomware attack becomes far more severe when it targets the server holding all your client financial records (Restricted Data) versus one that only hosts public marketing materials.
Your data security responsibilities don't end at your own front door. One of the most overlooked vulnerabilities for Canadian SMBs is supply chain risk—the threat posed by your vendors, partners, and suppliers. You might have fortress-like security, but if your payroll provider or a key software vendor is breached, your data could still be exposed.
The economic stakes are getting higher every year. Globally, trends like the rapid shift to cloud services and the rise of organized ransomware groups are putting immense pressure on businesses. This is especially true in our interconnected economy, where a single weak link in the supply chain can create a domino effect. You can explore more about how these interconnected risks are measured by reviewing the latest insights on regional pentesting strategies.
Evaluating your vendors' security practices is just as important as securing your own network. You need to ask them about their security certifications, breach notification process, and what controls they have in place to protect your information. A practical risk assessment must include this external view to be complete.
Once you've mapped out your data and pinpointed the risks, it's time to build your defences. Think of your risk assessment as the blueprint and security controls as the building materials. This is where your data security management program shifts from planning to tangible action.
The idea isn't to get tangled in a complex web of rules. It’s about creating a strong, practical foundation for security. You start with clear policies that set expectations for your team, then back them up with high-impact technical measures that actively protect your information. It's a simple one-two punch: policy sets the rules, and technology enforces them.
This process flow shows how identifying, classifying, and prioritizing your risks informs which controls you need to implement.
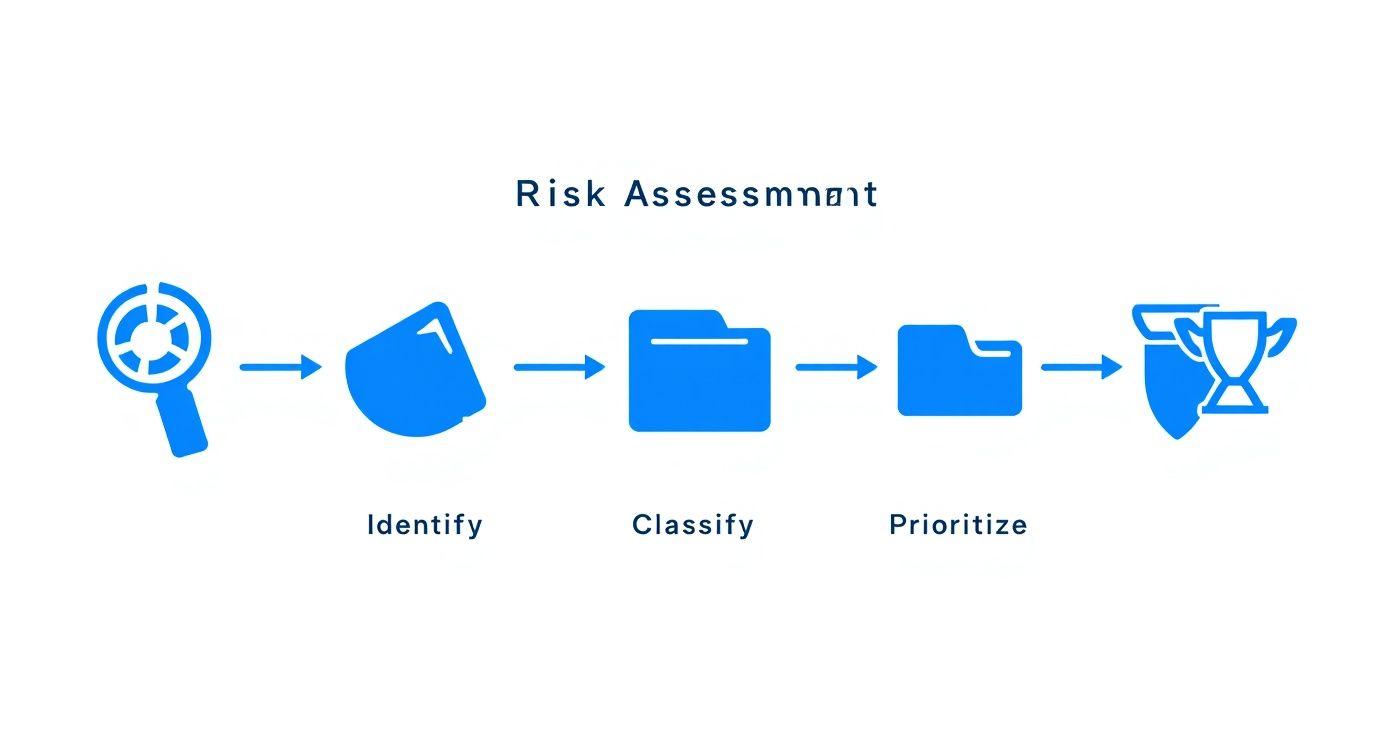
This model keeps your security efforts laser-focused on protecting what matters most against the most probable threats.
Before deploying technology, you need to define what good behaviour looks like. Foundational policies aren't just for checking a compliance box; they help create a security-conscious culture by ensuring everyone knows their responsibilities. For any medium-sized business, two policies are absolutely non-negotiable.
First is an Acceptable Use Policy (AUP). This document clearly explains how your team is permitted to use company technology—computers, networks, and internet access. It should be written in simple language, not technical jargon, and cover topics like password hygiene, prohibiting unauthorized software, and basic guidelines for handling company data.
The second is an Incident Response Plan (IRP). Realistically, no security system is perfect. Your ability to react quickly and effectively when something goes wrong can be the difference between a small hiccup and a full-blown disaster. Your IRP should outline the exact steps to take during a breach, from detection and containment to communication and recovery. For a look at what not to do, check out these 6 crucial cybersecurity mistakes and how to stop them.
A policy is only as good as its implementation. Don't just write these documents and file them away. Make them part of your employee onboarding and run brief, regular refreshers to keep security top of mind.
Once your policies are in place, you can bring in technical controls to enforce them automatically. These are the digital locks, alarms, and armoured vehicles of your security program. You want to focus on the measures that give you the most value.
Here is a quick look at some key technical controls and what they do for your business.
These controls form the backbone of a solid technical defence. Here’s a bit more on why each one is so critical.
Encryption: Think of it as a secret code. If a laptop is stolen or a server is hacked, encryption makes the data completely unreadable and useless to the thief. You should be encrypting data at rest (when it's stored on servers or hard drives) and in transit (when it's moving across your network or the internet). Modern operating systems and cloud services have made this much easier to implement.
Multi-Factor Authentication (MFA): Passwords alone are no longer sufficient. MFA adds a crucial second layer of security by requiring users to prove their identity with something they have (like a phone app or security key) in addition to something they know (their password). Enforcing MFA on all your critical applications—especially email and financial software—is one of the most effective security measures you can take. In fact, it can block 99.9% of automated cyberattacks.
Endpoint Protection: Every device connected to your network—laptops, desktops, servers, and even mobile phones—is an "endpoint." That also means it's a potential entry point for an attack. Modern endpoint protection solutions go beyond traditional antivirus. They use advanced techniques to detect and block malware, ransomware, and other sophisticated threats in real-time.
By combining clear policies with these powerful technical controls, you create a layered defence that dramatically improves your security posture. This approach ensures your data security management is not just a plan on paper, but a living, active system that protects your business 24/7.
Even with the best defences in place, you need a plan for when things go wrong. A security incident isn’t a matter of if, but when. How you respond in those first critical moments separates a minor issue from a full-blown catastrophe. This is where your monitoring, response plan, and recovery strategy truly prove their worth.
Think of continuous network monitoring as your digital alarm system. It involves using specialized tools to keep a close watch on your IT environment, looking for anything unusual—abnormal login attempts, odd data transfers, or signatures of known malware. Catching these red flags early gives you a vital head start to neutralize a threat before it spirals out of control.

When an incident is confirmed, panic is your worst enemy. A predefined Incident Response Plan (IRP) is your playbook, giving your team a clear, step-by-step guide to act decisively. A well-crafted plan moves through several key stages to ensure every action is coordinated and effective.
A solid IRP should always include these phases:
Consider a common scenario: a ransomware attack encrypts your main file server. Without a reliable Backup and Disaster Recovery (BDR) strategy, your options are grim. You can either pay the ransom (with no guarantee of getting your data back) or face a catastrophic loss of information.
Now, imagine that same scenario with a modern BDR solution. Instead of negotiating with criminals, you can simply wipe the infected server and restore a clean, recent backup. What could have been weeks of downtime and a massive financial hit becomes a manageable recovery process that might take only a few hours.
A great backup strategy isn't just about having copies of your files. It's about having a tested, reliable process for restoring your entire operation quickly and confidently. This is the ultimate safety net for your business continuity.
Finally, an incident response plan sitting on a shelf is useless. The only way to know if it will work is to practice it. Running regular drills, often called tabletop exercises, helps your team understand their roles and identify any gaps in the plan before a real crisis hits.
These drills simulate a security incident, forcing everyone to walk through the response process. This builds muscle memory and confidence, so when a real attack occurs, your team can execute the plan effectively. This level of preparation can also be a key factor in managing insurance claims, which is why understanding your coverage is so important. You can find more details in The Ultimate Guide to Cyber Insurance for Canadian SMBs.
Technical controls are essential, but your strongest security asset—or your biggest vulnerability—is your team. Your employees are the gatekeepers of your data. This means effective data security management is about transforming them from potential targets into a proactive "human firewall."
This goes far beyond a once-a-year training session. Too many organizations treat security training as a compliance exercise. But real security awareness isn’t about memorizing rules; it’s about building instincts. Your team needs to understand the "why" behind your policies so they can spot a real-world threat when it lands in their inbox.
When security becomes a shared responsibility rather than just an "IT problem," your entire defensive posture grows stronger.

The goal is to shift your team from passively hearing about security to actively defending against threats. This requires consistent, engaging training that mirrors the scams and tricks they will face. You want to empower your staff with the skills and confidence to not just identify but also report suspicious activity.
Here are a few practical strategies to get this going:
Run Engaging Phishing Simulations: Don't just tell employees what a phishing email looks like—show them. Regular, simulated phishing campaigns are one of the most effective training tools. They provide a safe space for people to make mistakes and, most importantly, learn from them. The key is to follow up immediately with constructive feedback that clearly points out the red flags they missed.
Focus on Social Engineering Tactics: Cybercriminals are masters of manipulation. Your training needs to cover the common social engineering tricks they use, like creating a fake sense of urgency ("Your account will be suspended!") or impersonating a trusted figure (like the CEO or a key vendor). Using real, anonymized examples makes these lessons stick.
Establish a Simple Reporting Process: Make it incredibly easy for employees to report anything that seems off. Whether it’s a dedicated email address (security@yourcompany.ca) or a simple button in their email client, the process must be frictionless. More importantly, create a culture where no one is penalized for a false alarm. It's far better to investigate ten harmless emails than to miss the one that is a genuine attack.
Empowering your team means treating them as part of the solution. When an employee reports a phishing attempt, celebrate it. This positive reinforcement encourages vigilance and makes everyone feel like they have a real stake in protecting the company.
You’ll know you’ve succeeded when safe practices become second nature. True security awareness isn't a one-time project; it's an ongoing program designed to keep security top-of-mind. This continuous reinforcement is what turns your team into a truly resilient human firewall.
Think about weaving security into your daily operations. You could share a "threat of the week" in team meetings or use digital signage in the office to display quick security tips. These small, consistent reminders are often more effective than an infrequent, multi-hour training session that everyone forgets by the next day.
Ultimately, you're aiming to create a workplace where every employee feels both responsible for and capable of defending the company's data. By investing in practical, ongoing training, you turn your biggest potential risk into your most powerful defensive layer.
Knowing when to ask for help is a sign of strong leadership, not weakness. For many businesses, there comes a point where the complexity of data security management outgrows what the in-house team can handle. Recognizing this tipping point is one of the most important steps you can take to protect your organization from increasingly sophisticated threats.
This is about more than just a lack of IT staff. The real signals are often more subtle. Perhaps your team lacks the niche skills to manage advanced security tools, or maybe the sheer volume of security alerts has become overwhelming. The biggest challenge for most is the need for 24/7 threat monitoring—a task that's nearly impossible for a typical SMB to manage alone.
Bringing on a managed security service provider (MSSP) isn’t just about outsourcing a task; it's about gaining a strategic partner. This relationship gives you immediate access to a team of dedicated security professionals whose entire job is to protect businesses like yours. They bring a level of expertise and advanced technology that would be incredibly expensive to build internally.
This approach offers several key advantages that can elevate your security posture almost overnight:
Partnering with an MSSP allows you to shift from a reactive security stance to a proactive one. It frees up your internal team to focus on core business initiatives, confident that your digital assets are being watched over by experts around the clock.
Choosing a provider is a critical decision. You need a partner who understands the specific challenges and regulatory landscape your business operates in. This is especially true as the security market continues to evolve. For instance, the Caribbean data security market is projected to reach US$5.67 million in 2025, driven by the adoption of AI-driven and cloud-based solutions to fight rising cyber risks. As you can learn from the latest market data, this trend highlights the growing need for specialized expertise that can manage a modern security stack effectively.
A good partner acts as an extension of your team, providing not just technology but also strategic guidance. They should help you align your security program with your business goals, making sure your investment delivers measurable protection. To get a better sense of what this relationship looks like, you can explore the various MSSP security services available.
Ultimately, the right partnership lets you focus on what you do best—growing your business.
When it comes to data security, many Canadian business leaders ask the same questions. Let's tackle some of the most common ones to provide clear insights for your own security journey.
The absolute first step—before buying any software or writing any policies—is a thorough risk assessment. It’s a simple but powerful truth: you can't protect what you don't know you have.
This process is about mapping your data landscape. You need to identify what sensitive data your business holds, determine exactly where it lives (on servers, in the cloud, on laptops?), and then realistically evaluate the threats it faces. This foundational step becomes the blueprint for your entire security program, ensuring you invest your time and money where it will have the biggest impact.
Canada's Personal Information Protection and Electronic Documents Act (PIPEDA) elevates data security from a best practice to a legal requirement. The act legally obligates your organization to protect personal information with appropriate safeguards.
This means your security program must be strong enough to actively prevent unauthorized access, disclosure, or loss of both your client and employee data.
A failure to meet PIPEDA's standards can lead to hefty fines, mandatory public breach notifications, and serious damage to your reputation. It makes robust data security a non-negotiable part of doing business in Canada.
While every business owner can and should implement basic security hygiene, the reality is that the threat landscape is incredibly complex and changes almost daily. The tactics cybercriminals use are constantly evolving to bypass simple defences.
Working with a managed security provider gives you access to specialized expertise, 24/7 monitoring, and advanced security tools that are often beyond the budget of a typical small or medium-sized business. Think of it less as outsourcing a task and more as gaining a dedicated security partner. This relationship allows you to build a proactive defence against sophisticated threats, so you can focus on what you do best: running your business.
At CloudOrbis Inc., we provide the expert guidance and 24/7 protection your business needs to thrive securely. Stop reacting to threats and start preventing them. Learn more about our managed cybersecurity services.

December 15, 2025
Managed IT Services for Alberta Private Career CollegesDiscover managed IT services for Alberta private career colleges. Boost security, compliance, and student success with a dedicated IT partnership.
Read Full Post
December 15, 2025
Small business it support edmonton: A Guide for Local Business LeadersDiscover small business it support edmonton options with clear pricing, expert guidance, and efficient IT solutions for growth.
Read Full Post
December 14, 2025
Small business it support edmonton: A Guide for Local Business LeadersDiscover small business it support edmonton options with clear pricing, expert guidance, and efficient IT solutions for growth.
Read Full Post